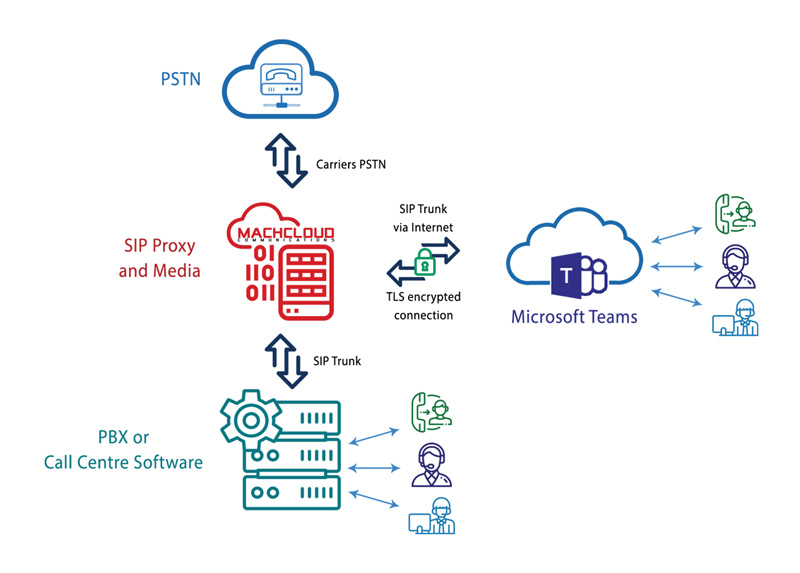
Microsoft Teams Direct Routing is being opted as the most recent business collaboration solution in the realm of digital communication. IT experts who deploy Direct Routing are aware of SBC security issues that arise as soon as they deploy the solution in place. A secure VoIP solution is the ultimate necessity of a company to thwart the increasing VoIP attacks emerging each day. Let’s have a look at how Microsoft deals with SBC security in its Microsoft Teams Direct Routing Solution.
The “friendly” attacks during configuration
An IT communications expert who was hired to deploy Microsoft Teams Direct routing in a cloud business, narrates his experience:
“While I was deploying Microsoft Teams Direct Routing with SIP trunks and a Session Border Controller (SBC), I happened to sense various SBC security vulnerabilities soon after I turned up the public interface. Long before the Teams configuration was complete there appeared a number of OPTIONS requests and huge SIP traffic from unknown sources. This traffic was supported by IP addresses trying to connect to my systems from around the world via malicious SIP scripting and scanning utilities. It was an alarming situation for me. Headers like “SIP Vicious”, “friendly-scanner”, and “PPLSIP”.
This scenario is not a unique one. All over the internet, attackers are in search of vulnerabilities. While SBCs are scanned in order to attempt hijack calling capabilities, admins can take this opportunity while deploying Microsoft Teams Direct Routing to configure and test the security rules provided by Direct Routing. There are two ways to secure your system: by configuring firewall and using Malicious Signatures feature.
ALSO READ:
Teams Direct Routing solutions to boost your business productivity
A properly configured Firewall, is your best friend forever
There are options to configure a Firewall for better security. All you have to do is configure the rules properly in the following manner:
- Exclude the LAN interface from Firewall list
- Allow external DNS lookups
- Allow Teams traffic
- Allow Signaling and RTP traffic
- In the final step, configure using: Block All others option.
Once these configurations are in place, you will no longer see or experience any malicious attempts. In fact, you will be able to see the number of attempts being blocked/dropped is increasing.
The Malicious Signatures feature for better security
A Malicious Signatures feature blocks all the attempts coming from malicious signatures and only allows the attempts from legitimate signatures. To make use of this feature, the admin has to configure a message policy. After this he has to malicious signatures database. Using this message policy, you can drop malicious SIP messages and set well defined limits. This policy can be assigned to the concerned SIP trunk.
ALSO READ:
Insight to employee experience with Microsoft teams and MachCloud
MachCloud Direct Routing powered by Microsoft Teams
MachCloud is a robust digital communication platform offering Teams Direct Routing, Cloud PBX, SIP Trunking and a multitude of business communications solutions like MachCloud and MachCloud Solution for Microsoft Teams. Resellers have a chance to boost up their revenue streams with MachCloud’s Office 365 reselling. With MachCloud’s direct routing, you can experience the true essence of enterprise calling with a variety of features like staying in control of your calls, memos and many other services both for both local and international clients. It is an all-in-one telephony platform for modern day business collaboration needs.
Get your hands-on Microsoft Teams Direct Routing via MachCloud and experience the top-notch business collaboration solution for better business productivity.